Estimated Savings: > $50,000 in potential losses averted
Executive Summary
Cyvocate identified and reported a critical payment logic flaw in a leading fintech platform. The vulnerability allowed attackers to purchase $100 worth of credits while paying only $1. If exploited at scale, this loophole could have caused substantial financial losses and severe reputational damage.
By promptly detecting and validating the issue, Cyvocate helped the client secure its transaction pipeline, protecting both its revenue and customer trust.
The Challenge
Digital payment platforms face constant threats where small validation errors can lead to catastrophic financial exposure. During a routine security assessment, Cyvocate uncovered a flaw in how the application processed recharge requests with its Internet Payment Gateway (IPG).
The system failed to enforce consistency checks between the payment amount deducted from the customer and the recharge amount credited to the account
The Exploit Scenario
Through controlled testing, our team demonstrated the vulnerability:
- Legitimate Flow: User pays $100 → Receives $100 credit.
- Exploit Flow: User pays $1 → Receives $100 credit.
By repeating this manipulation, attackers could have scaled the exploit to credit $50,000 worth of funds for just $500 in real payments.
Vulnerability Discovery
The application under review provided a recharge feature, where users could enter an amount and proceed to payment through an IPG. During traffic inspection with Burp Suite, our team observed that the application sent multiple requests before finalizing the transaction with the gateway.
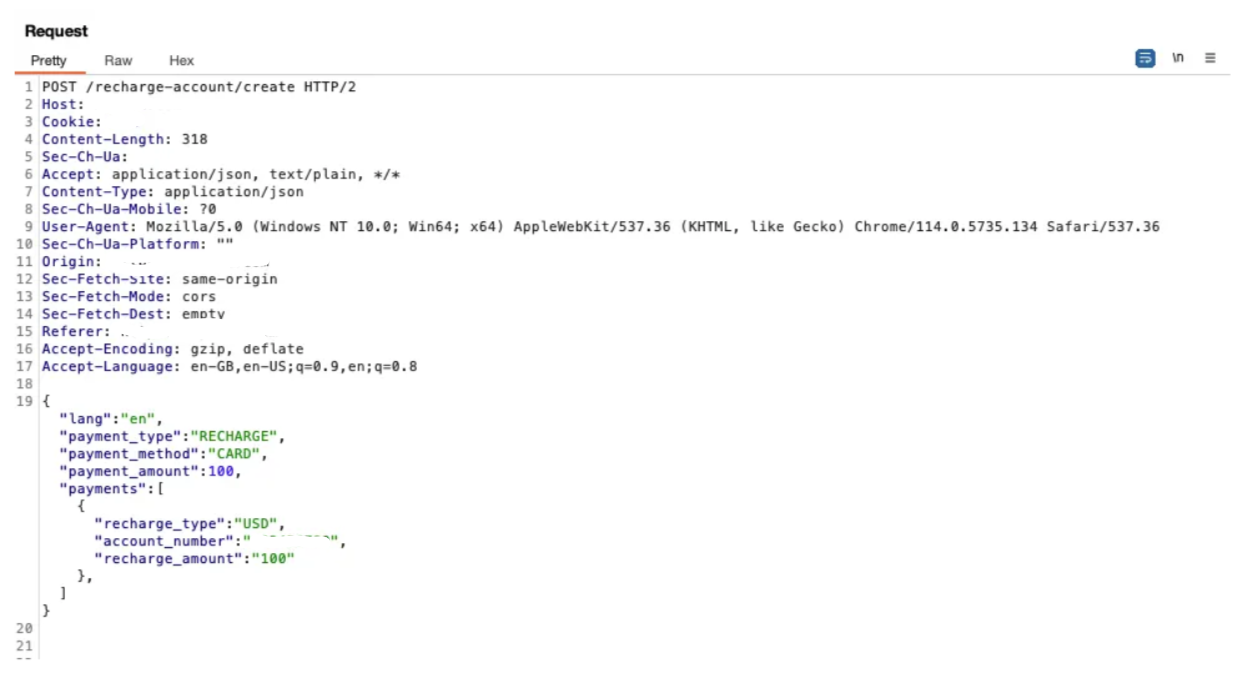
Two critical parameters were identified:
- payment_amount → The amount deducted from the user’s credit card.
- recharge_amount → The amount credited to the user’s account.
The flaw lay in the lack of validation on the payment_amount parameter. By manipulating these values, we were able to charge the card only $1 while simultaneously crediting $100 to the user’s account.
Attempts to set the payment amount to $0 failed at the IPG due to invalid input. However, setting payment_amount = $1 and recharge_amount = $100 successfully processed the transaction, confirming the vulnerability.
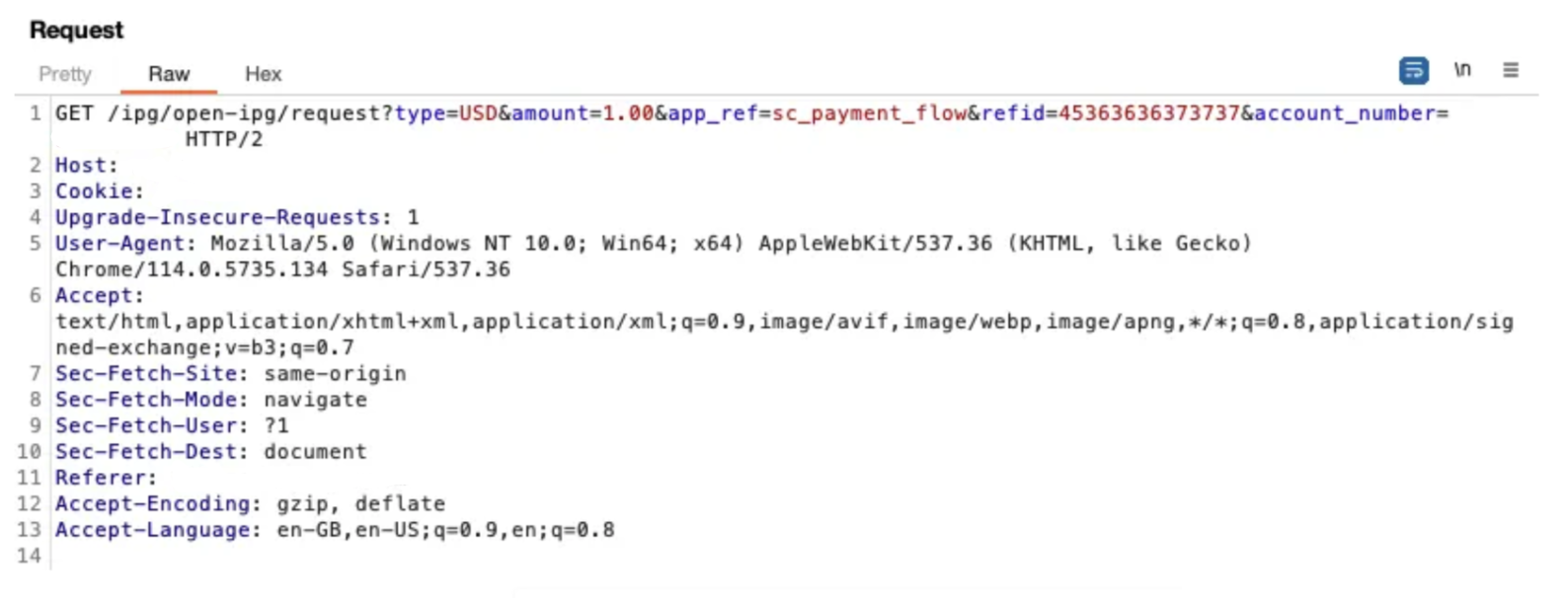
Through controlled testing, we validated this behavior at scale—up to $50,000 credited for just $500 in payments—before responsibly reporting the issue to the affected organization.
Impact & Risks
The implications of this vulnerability were severe:
- Direct Financial Losses → Attackers could exploit the flaw for unlimited account credits while paying only a fraction of the cost.
- Fraudulent Transactions → The system’s integrity was compromised, making it susceptible to exploitation at scale.
- Reputational Damage → A public disclosure or mass exploitation could erode customer trust and damage the brand’s credibility.
Recommendations
CYVOCATE recommended the following remediation measures:
- Input Validation & Logic Enforcement
- Ensure consistency between
payment_amountandrecharge_amount. - Validate all transaction data at both the client and server levels.
- Ensure consistency between
- Comprehensive Security Testing
- Conduct regular code reviews and penetration tests to identify similar flaws.
- Integrate automated validation mechanisms within the payment pipeline.
- Transaction Monitoring & Alerts
- Implement anomaly detection to flag irregular recharge-to-payment ratios.
- Continuously monitor financial transactions for suspicious patterns.